Linux permissions determine who can access, modify, and run files. Mastering permissions is key to system security and daily Linux usage.
Before starting make sure ur linux is ready.
- Ubuntu: ubuntu.com/download
- Debian: debian.org/distrib
- CentOS Stream: centos.org/download
- AlmaLinux: almalinux.org/download
- Talkecho full toturial: Click here
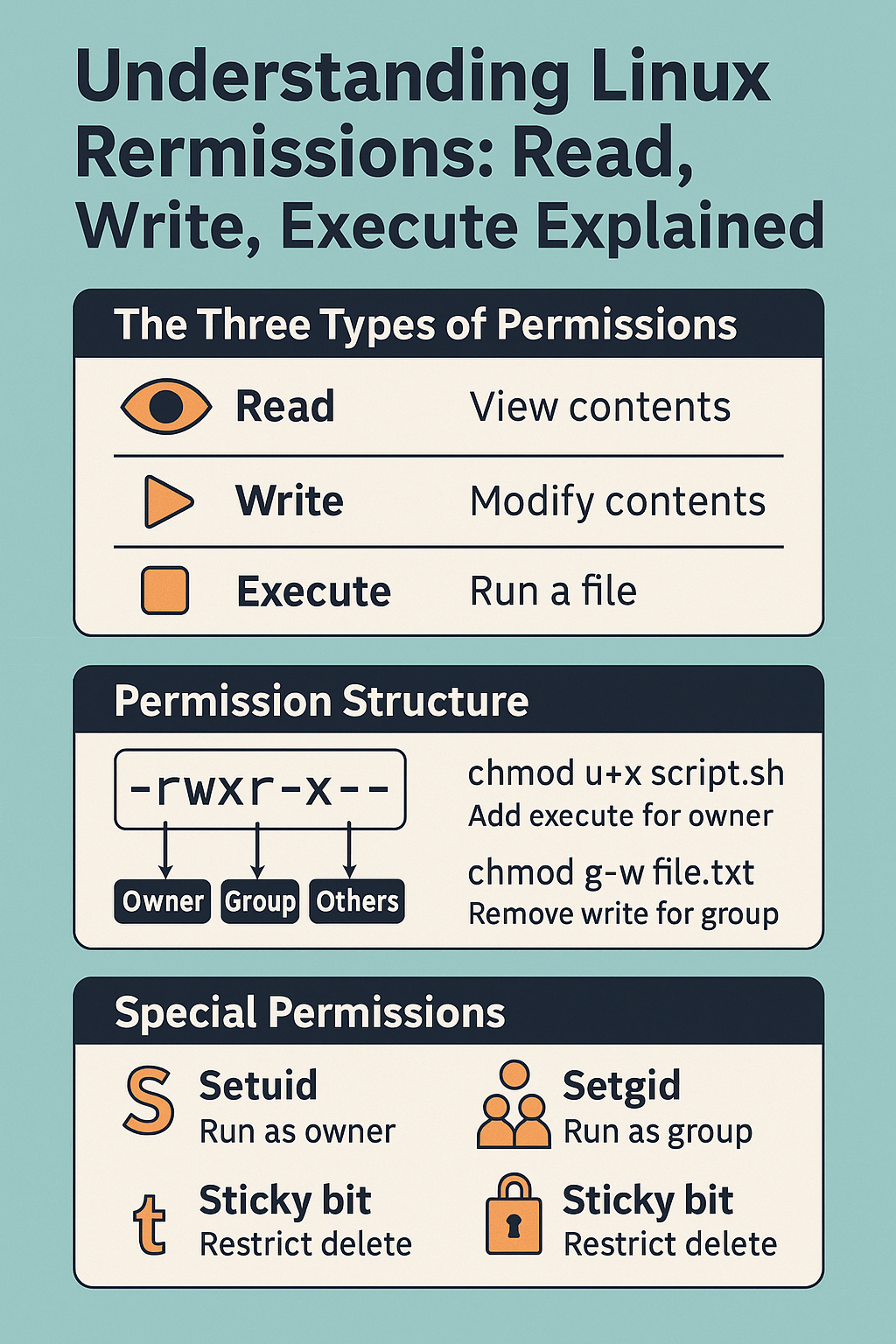
1) The Three Types of Permissions
- Read (r): View the contents of a file or list files in a directory.
- Write (w): Modify or delete a file; add or remove files inside a directory.
- Execute (x): Run a file as a program or access the contents of a directory.
Example output from ls -l:
-rwxr-xr-- 1 user group 1024 Jan 18 10:00 script.shThis means:
- Owner: read, write, execute
- Group: read, execute
- Others: read
2) Permission Structure
The 10-character string from ls -l is structured like this:
[-][rwx][rwx][rwx]
| | | |
| | | +-- others
| | +------- group
| +------------ owner
+---------------- file type (- = file, d = directory, l = link)3) Changing Permissions
Use chmod to adjust file permissions.
# Add execute permission for owner
chmod u+x script.sh
# Remove write for group
chmod g-w file.txt
# Grant all permissions to everyone
chmod 777 test.txtNumeric mode:
chmod 755 script.shBreakdown: 7 = rwx, 5 = r-x, 5 = r-x.
4) Changing Ownership
# Change owner
sudo chown alice file.txt
# Change owner and group
sudo chown alice:devs file.txtchgrp changes only the group:
sudo chgrp devs file.txt5) Special Permissions
- Setuid (s): File runs with owner privileges.
- Setgid (s): File runs with group privileges; new files in directory inherit group.
- Sticky bit (t): On a directory, only the file’s owner can delete it (e.g.,
/tmp).
# Add sticky bit to /shared
sudo chmod +t /shared6) Best Practices
- Use least privilege: avoid
777. - Restrict sensitive files to root only (
600for configs). - Audit with
find / -perm -4000for setuid binaries.